I decided to write this series to help a friend of mine better understand how to secure herself against creepy ex-boyfriends who knew everything about her. Since I am a network security expert, she asked me my advice and I realized that I should probably write a blog about it and never did. While none of this is female specific, it is something that single females should do to secure themselves and their lives in the modern age. Ever since I got involved with computers, I have always been interested in security and this probably stemmed from running a BBS at 300 baud. As computers progressed and I moved in to the corporate IT World the focus on Data availability, integrity and security all became a focal point. Emphasis was put on ensuring that users stored all data and documents on the server so that it could be secured and backed up. While I was focusing on security the consumer world was introduced to windows without any security at all. Users relished the freedom and ridiculed the lack of security.
Most people are of the misguided belief that there is nothing of value on their computer and that they have nothing to worry about on their computers. I am telling you to not be so sure about that and you really do not have to give up any freedom to make things a little more secure. I am going to explain why you should adopt these practices and then how to implement them and get used to using them. The idea is to keep you safe online and safe if someone steals your computer or smart phone. I will use real language and terms and try and explain them in everyday terms so that you can understand what the goal is and exactly how it is accomplished.
Around 2004 I got to see the seedier side of computer based crime that dealt with identity theft and fake documents. Someone who had been shown the basics by someone showed them to me. Using Photoshop he showed me the template for the new California Drivers License that would take effect in January, this being December. He then used the webcam on the notebook to take my picture and using Photoshop placed it in the correct places and onscreen it looked like it came from the DMV. We used all of my real information and he showed me the process to make an ID. First he printed the main layer on white paper. Then he printed another layer on clear transparency film and then another and finally the back layer. Each layer was cut to the precise size and then a clear epoxy was used to glue the back to the back of the base layer. Then each subsequent layer was glued on the top. When everything was complete it looked just like the real ID minus the gold printing. He then took this foil paper, placed it on the top and ironed it with an iron. When he removed the foil even the gold printing was there. The only thing that didn’t work was the magnetic strip.
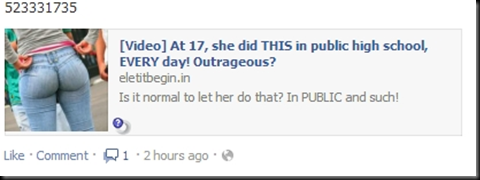
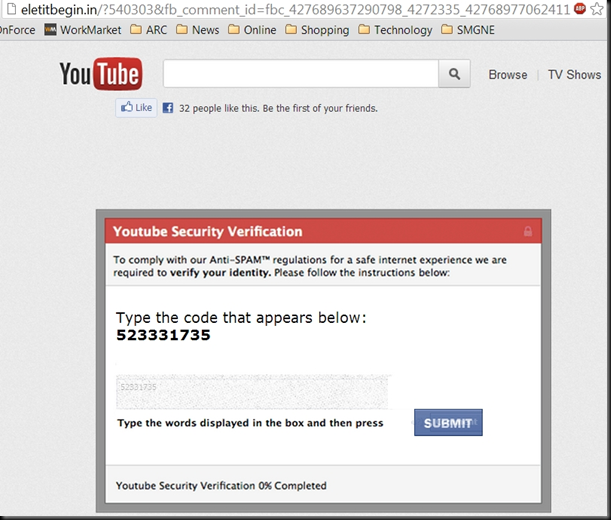
This was an entry level setup and the IDs it made would pass all rudimentary inspection if the maker paid attention to all of the details and took their time to ensure each step was perfect. I can only imagine what an artist with even more tools could accomplish in the same time. That being said, this made me realize how easy identity theft really is and that is the first area I will focus on. Ironically the same methodology used for this can also help ensure that an overly possessive boyfriend cannot snoop on you as easily either. A girl has to have her secrets. I have also been asked multiple times by clients over the years for assistance in personal matters that involved computer security and forensics. A friend contacted me today and explained the situation his friend was in, she was evidently somehow involved with someone or friends with someone who first tech-raped her and is now holding her tech-hostage. What I mean by this is he helped her setup her iPhone to sync with her ISP email and in doing so, he gained access to her passwords. He allegedly has hijacked her Facebook page and made inappropriate posts. So in the middle of the first draft of this blog, I began discussing this with him and offering advice.
I set my cell phone as a cell phone and only point of contact with the people that I do business with. I use a Patelco, a credit union, instead of a bank. I keep the address on most of my financially related information at an address other then my home address. This buffers and protects my identity because the only one with this other address are my creditors. I try and opt for online billing as often as possible. I download and save or print a PDF version of the bill and save it in a folder on my hard drive named yyyymmdd-accountname.pdf and then at the end of the year I zip all of the previous years up and leave the zip folder named yyyy–accountname.zip. I use this kind of archiving for everything. I save my camera phone photos by year and separated by decade. But I am lazy about backups, and continue to be so even though I have lost so much data to hardware failure.
Let’s get some things on the table: I do not trust the cloud for many reasons the most important of which is that it is for profit and that means they will change the terms and conditions at anytime and you have to agree to them and the second is most of them indemnify themselves from liability regardless of their culpability. They also often have weird clauses about who actually owns the information being stored on their cloud. But that is another story and blog.
Most online services and websites require a password although now it seems like there are two major providers and two minor providers of cross site logins: Twitter and Facebook followed by Microsoft and Google. I have personal and professional accounts at AOL/AIM, ICQ, Microsoft, Google, Yahoo and have Facebook, My Space and Linked In. All of these require passwords. To add to that complexity, I have my main email address: sgoldfein@gmail.com as valid addresses for AIM, MSN, and Google. Yahoo uses sgoldfein@yahoo.com and I also have an MSN for sgoldfein@hotmail.com. These all require unique secure passwords and a way to remember them securely and that’s just the beginning.
There is this myth that there is a need to constantly change your password for security and integrity reasons although I am not sure where this ideology came from but Microsoft did a massive study over a several year period of time and realized that forced password changes on a random basis provided absolutely no more security then using the same password for the entire period of time. They also found that the help desk spent far more time resetting passwords soon after the change then at any other time and that there were little to no password resets necessary when the users were not required to change their passwords. So in conclusion: requiring random password changes doesn’t increase security but it does reduce productivity and increase help desk costs.
The one thing there is no myth about is choosing passwords and securing them after we choose them. When I first started life online, I used one password or a derivative of it on every BBS I joined. I quickly learned that this was a stupid move and an asshole sysop could find out your password and logon as you somewhere else. About 10 years ago I found a program called Roboform and it revolutionized how I did passwords because it allowed me to carry my list of passwords with me on a Flash Drive or my Cell Phone encrypted from prying eyes. Roboform has come a long way and there are versions available for Windows, Macintosh, Cloud Based, Android, and IPod/IPad. Roboform integrates with most browsers, although right now it does not work with Maxthon like it is supposed to but that’s not a show stopper.
Download the installer from the website above and save it to the Downloads folder on your computer and then navigate to that folder using My Computer or Windows Explorer. Select and double click on the installer file and it will display the following screen:
Now before we proceed you need to be thinking about your ‘Master Password’ as this is the most important password on your system because it is the one that will be used to secure your other passwords and data. I recommend taking your favorite verse from the bible, or a song or first paragraph of a book you know by heart or any passage of text you know by heart. Recite it in your head memorizing the first letter of each word until you can just say the letters without thinking about it. That is your private master password and you should never tell anyone what it is. I usually add some random number for letter substitutions within as well. Use this password in Roboform to secure your passwords.
Notice I have checked the Show Advanced Options checkbox. I will explain each of the options as we proceed with the installations so you will understand what effect they have on the overall program. I am doing an upgrade and not a new install so there might be a slight variance in the process from what you see here.
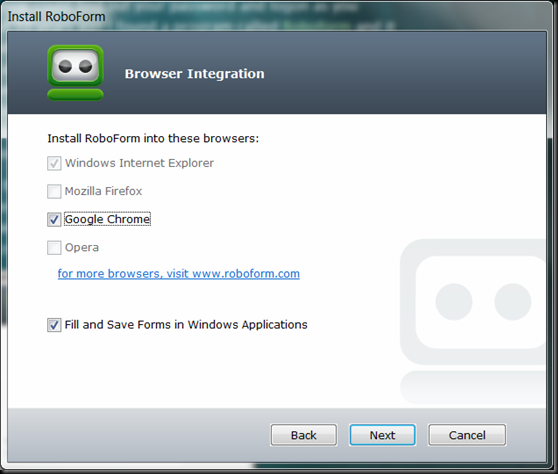
The installed and active browsers will have the Roboform Toolbar connectors installed. This allows Roboform to display a toolbar in the browser that let’s you click a button on it to fill in the username and password. It doesn’t appear in screenshots of Chrome for some reason either, so I can’t post a screenshot. If the browser is installed the option to install the add-on becomes active.
I started using Chrome for one reason and one reason only, it was fast, stable and it was NOT IE or Firefox. I would have used Opera but it did not have Roboform support. As soon as Maxthon and Roboform work together, it will be my browser of choice.
Notice there is also an option to Fill and save forms in Windows Applications and this is a hit or miss. IBM / Lenovo used to have a password manager that they bundled in their security apps that hit this like no other. It could fill the passwords in any windows app. It is hit or miss with this and it does not work with games like Lord Of The Rings Online. I select it anyway in the hopes hey slowly improve upon it like they have everything else. 
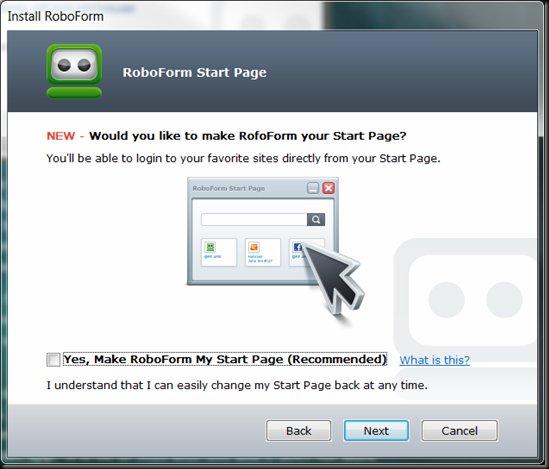
This is an annoyance because you really cannot utilize Roboform without purchasing it and as such I do not want it to hijack my start page. Other’s might feel differently and I might change my mind in the future should I accidentally forget to uncheck it.
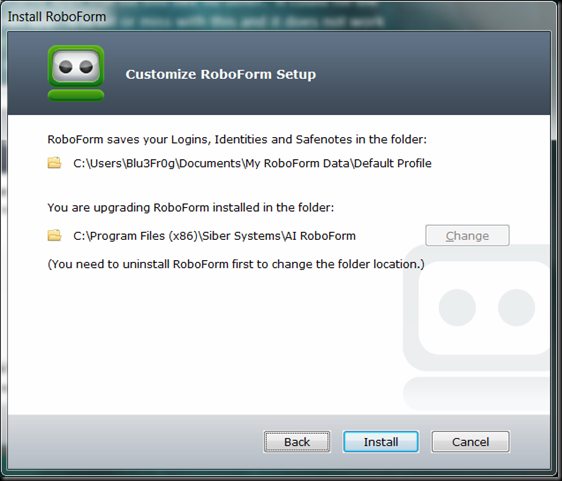
Since I have already installed and Roboform is running, I cannot change these options and there isn’t really a reason I can foresee to want to.
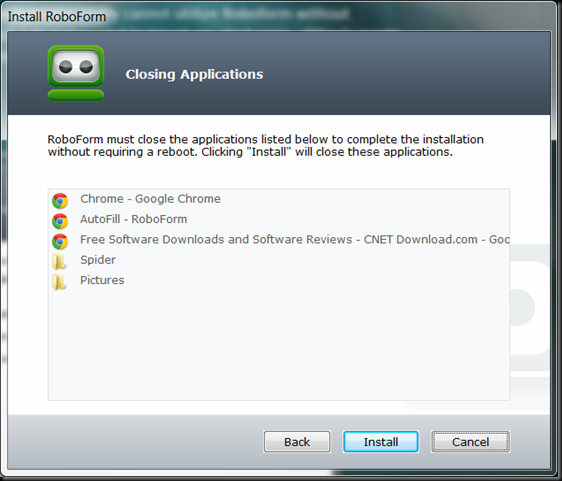
It wants me to close all my browser and windows explorer windows.
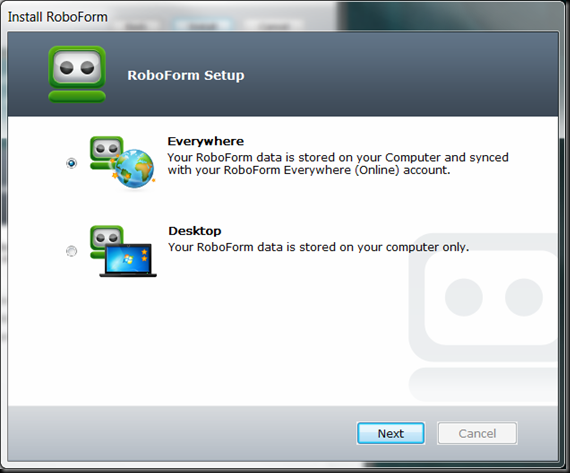
Do you have Android or an I pad or an IPhone? If so then you will want to make a temporary account this one time before you add any new passcards.
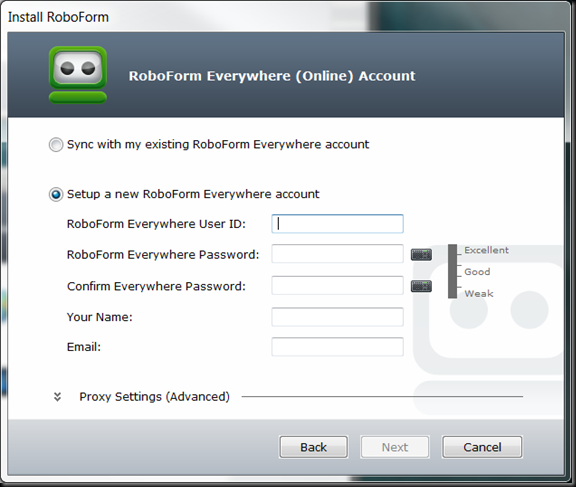
Fill in the information above and create your user account. If it offers to make a passcard, do so. Then follow instructions to finish the install and perform the first sync.
Then load the Roboform options by right clicking the little green RoboForm icon in the tray next to the clock and selection options.
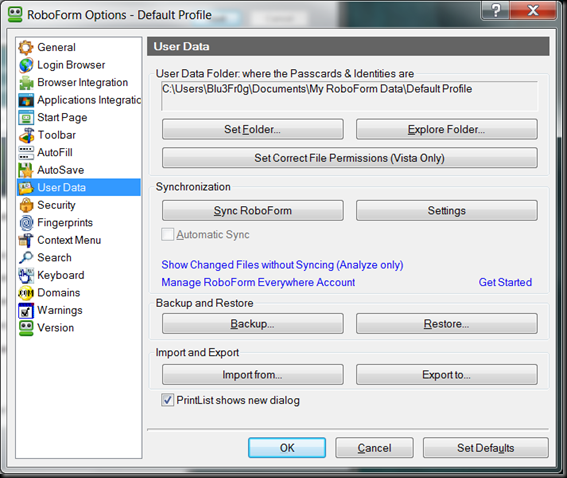
Select User Data and click the Settings Button.
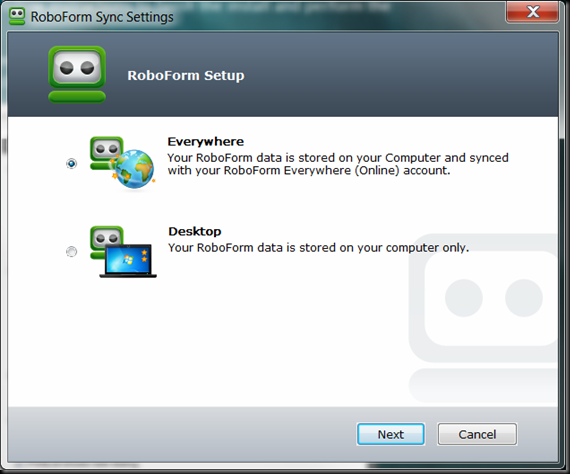
Choose Desktop and follow the prompts to finish. Now just go and login to your favorite sites like Facebook and Yahoo. I would use the toolbar option to generate random passwords to generate new random passwords and use a different one for each site.
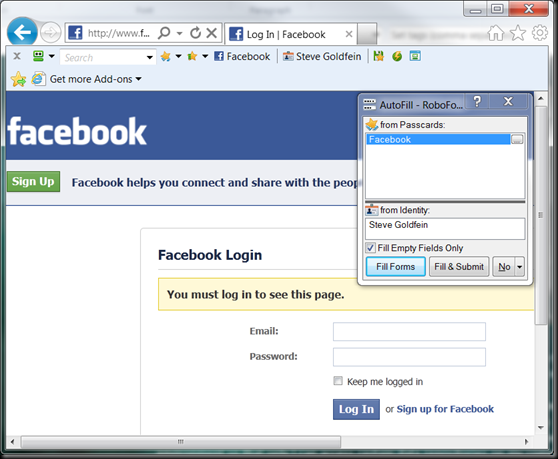
If this were the first time I visited Facebook it would wait for me to fill the username and password and then it would ask if I wanted to save it. Make sure the Keep Me Logged In checkbox is checked and remains that way when saving the passcard. Finally I would make sure you use a Windows Password that no one knows, you can change your password by pressing Control + Alt and the Delete key all at the same time. Then select Change Password and follow the prompts.
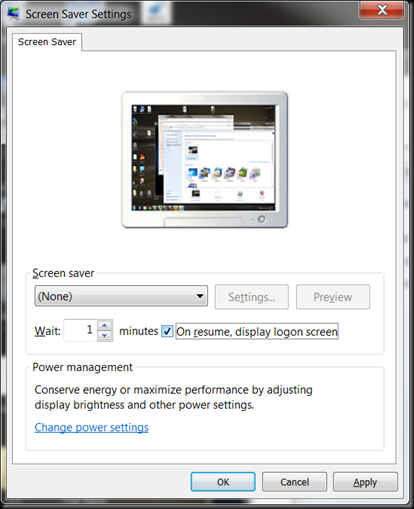
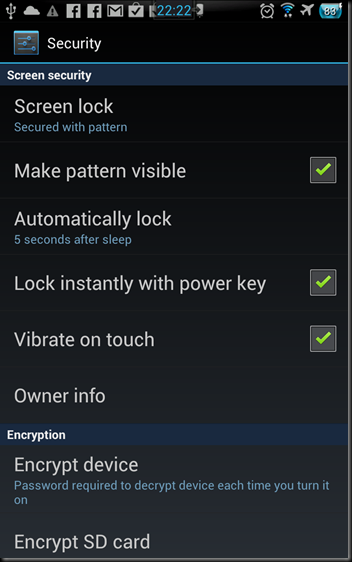
Finally, change Windows to ask for a password on Resume. This will make Windows ask for a password when the screensaver comes on. This means if you walk away or get distracted that someone can’t get access to your computer. By force of habit I lock my computer. Another Tech pranked me and I decided to never let it happen again. He basically took a screen shot of my desktop with all the applications minimized. He then used the control panel to hide the desktop icons and hid the start menu. This was back with Windows NT and random lockups before SP3. Change your passwords and use Roboform. I will cover the android and portable versions in the future. In Windows Vista and 7 you can hit Control+Alt+Delete and select Lock Computer or just press the Windows Key and L at the same time to do it. I usually forget and just let the screen saver take over.